Cyber Risk Management
and Transformation
Evolve From Spreadsheets to Automation
Let’s Evolve Your Insider Risk Program
Having an effective insider risk program is essential to ensure the security of your organization. By taking the time to develop and refine your insider risk program, you can limit the potential risks that come with having employees or contractors with access to sensitive data.

Navigate the Risk Renaissance
The Risk Renaissance has ushered in a new era of risk management, where organizations are taking an increasingly proactive approach to managing risk
and leveraging technology to do so. As organizations navigate this new landscape, they must consider the implications of their decisions, as well as the potential
benefits and risks associated with them. Risk management has become an
integral part of modern business, and organizations must develop a
comprehensive strategy to identify, assess, and manage risks.
Organizations must understand the implications of new technologies and changing regulations, and they must be prepared to respond accordingly. For example, organizations must understand the implications of blockchain technology,
artificial intelligence, and big data, and how they can be leveraged to better
manage risk. Additionally, organizations should be aware of the ever-evolving regulatory landscape and what changes may be necessary to comply.
Organizations must also develop an effective risk assessment and management process. This process should involve a thorough evaluation of potential risks, identification of the most significant risks, and development of strategies
to mitigate those risks. Additionally, organizations should establish a system
for monitoring and reporting on risks, and for responding to unexpected events.
Finally, organizations should develop a culture of risk management, and
ensure that risk management is embedded in every aspect of their operations.
This includes developing a risk-aware culture, and providing employees
with the necessary training and resources to effectively manage risk.
Overall, organizations must be prepared to navigate the Risk Renaissance and
the changing landscape of risk management. By developing an effective risk assessment and management process, understanding the implications of new technologies and regulations, and creating a culture of risk management, organizations can ensure that they are prepared to successfully navigate
the Risk Renaissance.
Why are organizations missing insider threats?

Lack of Awareness
Organizations often fail to recognize the potential
for insider threats and how they can exploit access
to sensitive data.

Poor Authentication
Organizations may not have the necessary authentication and authorization measures in place to protect against unauthorized access.

Poor Security Practices
Without proper security measures in place, organizations are vulnerable to malicious acts by insiders.

Unclear Policies
Organizations may not have clearly defined rules and processes that govern access to sensitive data or the consequences of any violations.

Failure to Monitor
Organizations may not have the right systems in place to detect malicious activity or the resources to monitor user behaviour.

Limited Resources
Organizations may not have the resources or personnel needed to adequately monitor and respond to potential insider threats.
Yet even as they embrace it, organizations still struggle with
At the dawn of a new era of risk management, the Risk Renaissance
has taken hold. It is a time when organizations are rethinking
their approach to risk, looking for new ways to identify and mitigate it.
The Risk Renaissance is not only about adopting a more comprehensive
and holistic view of risk, but also about empowering internal teams to
take ownership of risk management, creating a culture of accountability
and transparency.
The Risk Renaissance is about embracing the challenge
of managing risk, understanding the complexity of its interconnectivity,
and utilizing the latest technology and tools to identify and address it. Organizations must be proactive in their risk management, creating a
culture of continuous improvement and collaboration. They must also
embrace change and adapt quickly to emerging risks.
The Risk Renaissance is a call to action. Organizations must be proactive,
agile, and accountable in their risk management. By understanding and assessing risk in its entirety, organizations can create a secure and resilient environment, which can ultimately lead to greater success.
The Risk Renaissance is the answer to the age-old question:
how do you manage risk?
The answer is simple: with a renewed commitment and an eye toward
the future.

CYBER RISK MANAGEMENT STRATEGIES
At AVIH, we are committed to protecting our customers, their data, and our company’s data from any potential security threats. To ensure we are consistently meeting this goal, we are implementing a Security Awareness Program for all of our employees. This program is designed to keep our employees informed about the latest security threats and best practices for protecting our data. All employees will participate in regular training sessions that cover topics such as recognizing malicious emails and websites, password best practices, and other security-related topics. We also encourage employees to stay informed and practice safe online habits outside of the workplace. This includes using strong passwords, never clicking on unknown links, and being aware of potential scams. Additionally, all employees must adhere to our company’s security policies and procedures, which are outlined in the employee handbook. These policies are designed to protect our data and our customers’ data, so it is essential that all employees are familiar with them and follow them at all times. At AVIH, we understand that security threats can come from anywhere, so we take our security awareness program seriously. We are committed to protecting our data and our customers’ data, and we will continue to update and refine our program
Security policies are the foundation for any organization‘s security program. They provide the guidance and direction necessary for protecting valuable assets and information. Developing and maintaining security policies is essential for a successful security program. Security policies should provide clear definitions of acceptable and unacceptable use of the organization‘s resources. They should also provide guidance on how to handle security incidents and how to protect the organization from potential threats. Security policies should be designed to be comprehensive, effective and up–to–date. Developing security policies requires a thorough understanding of the organization‘s goals and objectives, as well as its security requirements. Security policies should be written in simple language that is understandable to all stakeholders. Security policies should also be regularly reviewed and updated to ensure they remain relevant and effective. Maintaining security policies involves regularly monitoring their implementation and effectiveness. It is important to ensure that the policies are being followed and enforced. Security policies should be regularly reviewed and updated to address new or changing threats. In summary, developing and maintaining security policies is essential to establishing a successful security program. Security policies should provide clear definitions and guidance, and should be regularly reviewed and updated to ensure they remain relevant and effective.
The success of any organization‘s security lies in the ability to implement and maintain effective access control policies. As threats become more sophisticated, organizations must be proactive in developing and enforcing access control policies that protect their assets and data. At its basic level, access control is the process of controlling who has permission to access, view, or modify a system or its data. Effective access control policies ensure that only authorized individuals can access data and systems and that data is protected from unauthorized access, misuse, and alteration. It is important for organizations to develop access control policies that are tailored to their specific needs. These policies should include information about who has access to which systems, data, and applications and the level of access they have. Access control policies should also include details about the authentication process, such as the type of credentials required and the frequency of password changes. Organizations should also consider implementing additional security measures such as multi–factor authentication, encryption, and data loss prevention. These measures can help to protect data and systems from unauthorized access and misuse. When developing access control policies, organizations should consider their current environment, the type of data they need to protect, and any foreseeable risks. It is also important to regularly review and update
Security training is essential for any business. It helps protect your staff, your customers, and your business. By providing comprehensive security training for your staff, you can help ensure that your business is secure and that your staff are aware of the risks posed by cyber–attacks, data breaches, and other security threats. At AVIH, we are committed to providing our employees with the best possible security training. We believe that security is paramount to the success of our business and we strive to ensure that our employees have the knowledge and skills they need to keep our customers and our business safe. Our security training program covers a wide range of topics, including: • Overview of the Security Threat Landscape – We’ll help your staff understand the current threats posed by hackers, malware, and other malicious actors. • Security Policies and Procedures – We’ll teach your staff how to implement and enforce security policies and procedures. • Data Protection – We’ll show your staff how to protect customer and company data from unauthorized access and use. • Security Awareness Training – We’ll provide your staff with the education and resources they need to stay informed about the latest security threats. • Security Testing and Auditing – We’ll help your staff understand the importance of regular security testing and audits. At AVIH, we understand that security is essential for any business. We strive to provide our employees with the best possible security training to help ensure that our customers and our business are protected. If you have any questions or would like to learn more about our security training program, please don’t hesitate to contact us. We look forward to helping you create a secure environment for your business.
Risk assessments are a critical part of any business’s success. They help identify potential risks and plan for expected outcomes, both positive and negative. To ensure your business remains on the right track, it’s important to perform regular risk assessments. A risk assessment is a process of identifying, analyzing, and responding to potential risks that can have an impact on your business. Through a risk assessment, you’ll be able to develop strategies to reduce or eliminate risks, as well as plan for potential opportunities or challenges. When performing a risk assessment, start by identifying the risks associated with your business. Consider areas such as operations, finances, personnel, and technology. Once you’ve identified the risks, analyze them to determine the potential impact of each. Finally, develop strategies to address each risk, including mitigation plans and action steps. Regular risk assessments are essential for managing risk and keeping your business on track. They are a proactive approach to preventing potential disasters and ensuring you are prepared for whatever comes your way. With a regular risk assessment, you can identify potential risks, analyze the impact they may have on your business, and develop strategies to mitigate or eliminate those risks.
Creating and enforcing strong password policies is essential in protecting your data and digital assets. To ensure the secure protection of your accounts, here are some best practices for implementing strong password policies:
1. Require strong passwords: Passwords should contain a combination of upper and lowercase letters, numbers, and symbols. Passwords should be at least 8 characters long and be changed regularly.
2. Prohibit the reuse of passwords: Users should not be allowed to reuse their passwords across multiple accounts. Require users to create unique passwords for each of their accounts.
3. Enforce password complexity rules: Complex passwords are more difficult for hackers to crack. Passwords should include at least one upper case letter, one lower case letter, one number, and one symbol.
4. Implement two–factor authentication: Two–factor authentication adds another layer of security to your accounts by requiring users to provide additional verification, such as a security code sent to their phone, when accessing their accounts.
5. Restrict access to sensitive data: Only allow access to sensitive data to users who have the appropriate permissions to access it.
6. Regularly monitor account activity: Monitor accounts for suspicious activity and unauthorized access.
7. Educate your users: Make sure your users are aware of the importance of strong passwords and other security best practices.
By following these best practices, you can ensure the secure protection of your data and digital assets.
Secure your business with a powerful combination of firewalls and intrusion detection systems. With these tools, you can protect your network from unwanted intruders, while keeping your systems running optimally and securely. Firewalls can block access to malicious websites and applications, while intrusion detection systems can detect and alert you to any suspicious activity. With effective firewalls and intrusion detection systems in place, you can rest assured that your business is protected from the latest cyber threats.
At AVIH, we take data security seriously. We understand the importance of protecting sensitive data and the need for secure communication. To ensure the highest level of security, we have implemented several measures, including encryption and other data security methods. Encryption is a process used to protect data by scrambling it so that only authorized parties can access it. We use encryption protocols to protect all data in transit, making sure that data is not revealed to any unauthorized parties. We also use encryption to protect data at rest, ensuring that data stored on our servers is secure and inaccessible to unauthorized personnel. In addition to encryption, we also use other data security measures to protect our customers’ data. We regularly monitor our systems for any suspicious activity, and we use firewalls, malware detection, and network segmentation to protect against security threats. We also conduct regular vulnerability scans to identify any potential security issues and we audit our logs for any suspicious behavior. Finally, we have strict policies in place to ensure that our data security measures are followed. All of our employees are trained on data security and we have a culture of compliance. We also require all of our partners to adhere to our data security standards, and we regularly review and update our policies to ensure that our data remains secure. At AVIH, we take the security of our customers’ data seriously. Through encryption and other data security measures, we are committed to ensuring that all data is protected and secure.
At AVIH, we understand the importance of staying up-to-date with the latest software, operating systems, and applications. That’s why we are committed to regularly updating our products to ensure they are secure and reliable. Our team of developers and engineers are continuously working to provide our customers with the best solutions for their needs. With our regularly updating software, operating systems, and applications, you can be sure that your business is running at its peak performance.
Regular backups are essential to protecting the data that is important to you. With a proper backup system in place, you can ensure that all of your files and information are safeguarded no matter what happens. Whether you‘re dealing with natural disasters, hardware failure, or malicious attacks, regular backups can help you keep your data safe and recover it quickly. Investing in reliable backup solutions will give you peace of mind, so you can focus on running your business without worrying about losing important data.
Security audits and reports are essential tools for ensuring the safety and security of data, systems, and networks. When properly implemented, these audits and reports can help detect and prevent potential vulnerabilities, identify any malicious activity, and ensure that companies comply with relevant security regulations. To ensure the most effective security audits and reports, companies should first establish a comprehensive security policy. This policy should provide clear guidelines for security protocols and include detailed instructions for performing audits and writing reports. It is also important to thoroughly document the security measures that are in place, as well as any security–related incidents that have occurred. The next step is to perform regular security audits. Audits should be conducted on a regular basis to identify any vulnerabilities or weaknesses in the system. During this process, the auditor should assess the strength of the security infrastructure, the ability to detect and respond to threats, and the effectiveness of security procedures. The auditor should also analyze the security logs and maintain an audit trail. This audit trail will provide evidence of any security incidents that have occurred and help to identify any malicious activity. This audit trail can then be used to assess the effectiveness of the security measures that have been put in place. Finally, the auditor should create a comprehensive report that summarizes the findings of the audit. This report should include detailed recommendations for improving the security of the system, as well as any policy changes that may be needed. This report should then be shared with the appropriate stakeholders, such as the company‘s management team and security personnel. By implementing effective security audits and reports, companies can ensure that their data, systems, and networks are secure and compliant with relevant security regulations. This will help to protect the company from malicious attacks, safeguard sensitive data, and minimize the risk of data breaches.
Secure Network Segmentation is your key to creating a safe and reliable network infrastructure. With segmentation, you can isolate critical systems and protect sensitive data from outsiders and malicious actors. This way, you can maintain a secure network perimeter and prevent unauthorized access. Segmentation also makes it easier to detect and mitigate threats quickly, keeping your network environment safe and secure.
Secure your online accounts with multi–factor authentication. By using more than just a password to gain access to your digital accounts, you can protect yourself from data breaches, identity theft, and other cyber–related crimes. Multi–factor authentication adds an extra layer of security that ensures only you have access to your accounts and sensitive data. With multi–factor authentication, your passwords are no longer the only key to your digital safe.
Security Information and Event Management (SIEM) is an essential tool for any organization looking to protect their systems and data. SIEM provides real–time visibility and analysis of security threats, allowing organizations to proactively detect and respond to cyber attacks, threats, and vulnerabilities. With SIEM, organizations can gather, analyze, and investigate security events to identify and respond to potential threats more quickly and efficiently. With SIEM, organizations can gain a better understanding of their security posture and take the necessary steps to prevent data breaches and ensure their data remains secure.
Ensuring the security of your IT systems is an essential part of your organization’s operations. Regular vulnerability scanning and penetration testing can help you identify potential risks and mitigate them quickly. By performing regular vulnerability scans and penetration tests, you can detect weaknesses and vulnerabilities in your IT infrastructure that can be used to compromise your systems and data. With these tests, you can identify and fix any potential security flaws before they are exploited. Your organization should perform regular vulnerability scanning and penetration testing in order to ensure the security of your systems. Vulnerability scanning is the process of scanning your IT infrastructure for potential weaknesses. It can be used to detect common vulnerabilities such as unpatched software and open ports. Penetration testing is the process of testing the security of your system by attempting to gain access to restricted resources. It can be used to identify weaknesses in your system that could allow an attacker to gain access to your data or other critical resources. By performing regular vulnerability scanning and penetration testing, you can ensure that your systems are secure from potential threats. You can also detect any existing vulnerabilities quickly and take appropriate action to mitigate them. This will help protect your organization from security breaches and data loss.
By leveraging behavioral analytics, businesses can gain a deeper understanding of their customers and deliver more personalized experiences. By tracking customer behavior and analyzing the data, businesses can uncover valuable insights, identify trends, and optimize their products and services to meet the needs of their customers. With the help of behavioral analytics, businesses can gain a more complete picture of their customers and create more effective marketing strategies to increase engagement and drive sales. With the right insights, businesses can create a more personalized and targeted approach to their customers, leading to greater customer satisfaction and loyalty.
Network Access Control (NAC) is an important tool for any organization that needs to protect its data, resources, and networks from unauthorized access. NAC solutions provide a comprehensive approach to controlling who can access a network and what type of access they can have. By implementing a NAC solution, organizations can ensure that only authorized users have access to their network and can monitor and restrict any suspicious or malicious activity. NAC solutions are designed to work with existing network infrastructure and can be integrated into existing security policies and procedures. NAC solutions provide the ability to authenticate users, control access to network resources, and monitor network activity. NAC solutions also provide an additional layer of security by automatically applying restrictions and policies to new devices or users as they join the network. In addition to protecting against unauthorized access, NAC solutions can also be used to enforce policies and provide compliance with regulations. NAC solutions can provide automated reporting, alerting, and remediation of any violations or suspicious activity. This helps organizations to ensure that their networks and data remain secure and compliant with industry standards. By implementing a NAC solution, organizations can gain better control of their network, increase visibility into network activity, and improve the security of their data and resources. NAC solutions provide organizations with the ability to protect their networks and resources from unauthorized access, ensuring that only authorized users have access to sensitive data and networks.
Protecting your organization from cyber threats requires a well–developed incident response plan. An incident response plan is a document that outlines the procedures your organization will follow in the event of a cyber attack or any other type of security incident. This plan should include steps for mitigating the impact of the attack, recovering systems, and preventing future incidents. At its core, an incident response plan should provide clear guidance on how to respond quickly and effectively to any security incident. This includes how to detect, contain, and recover from the incident, as well as how to communicate with stakeholders. It should also outline procedures to help prevent future incidents from occurring. The key to a successful incident response plan is to ensure that it is regularly reviewed, updated, and tested. It is important to create procedures for regularly monitoring and addressing any changes in the environment that could lead to an incident. In addition, your plan should be tested regularly to ensure that it is up–to–date and includes the most current best practices. By having a comprehensive incident response plan in place, you can ensure that your organization is better prepared to handle any security incident, no matter how small or large. This will help protect your assets, maintain business continuity, and ensure that your organization is able to respond quickly and effectively.
Get Ahead of Your Insider Risks
Insider risks are a growing concern for organizations of all sizes. From large companies to small businesses, any organization with access to confidential customer or organizational data is a potential target for malicious insiders and other malicious actors. With the prevalence of insider threats, organizations must take proactive measures to protect their data and systems from potential threats.
One of the best ways to get ahead of insider risks is to develop an effective security strategy that addresses all potential insider threats. This involves establishing clear policies and procedures to ensure that access to sensitive data is limited to only those who need it. Additionally, organizations should consider implementing technology-based solutions such as identity and access management (IAM) systems to track and monitor access to data.
Organizations should also consider adopting an insider threat prevention program. This program should include training and awareness initiatives to help employees recognize and report suspicious behavior. Additionally, organizations should use data analytics to detect anomalous activity and investigate any identified threats.
Organizations should also consider conducting regular security audits to identify any potential vulnerabilities or weaknesses in their systems. Additionally, organizations should employ a team of security professionals to monitor and review security logs for potential threats.
Finally, organizations should consider partnering with a third-party security provider to provide additional monitoring and protection. This can help organizations identify potential threats and respond quickly if a malicious insider is identified.
By taking proactive steps to get ahead of insider risks, organizations can protect their data, systems, and customers from malicious actors. With the right security measures in place, organizations can be better equipped to prevent and respond to potential threats.
Govern your insider risk program
Protect your data, assets and people
Detect anomalous or risky behavior
Respond to potential incidents and recover quickly and effectively
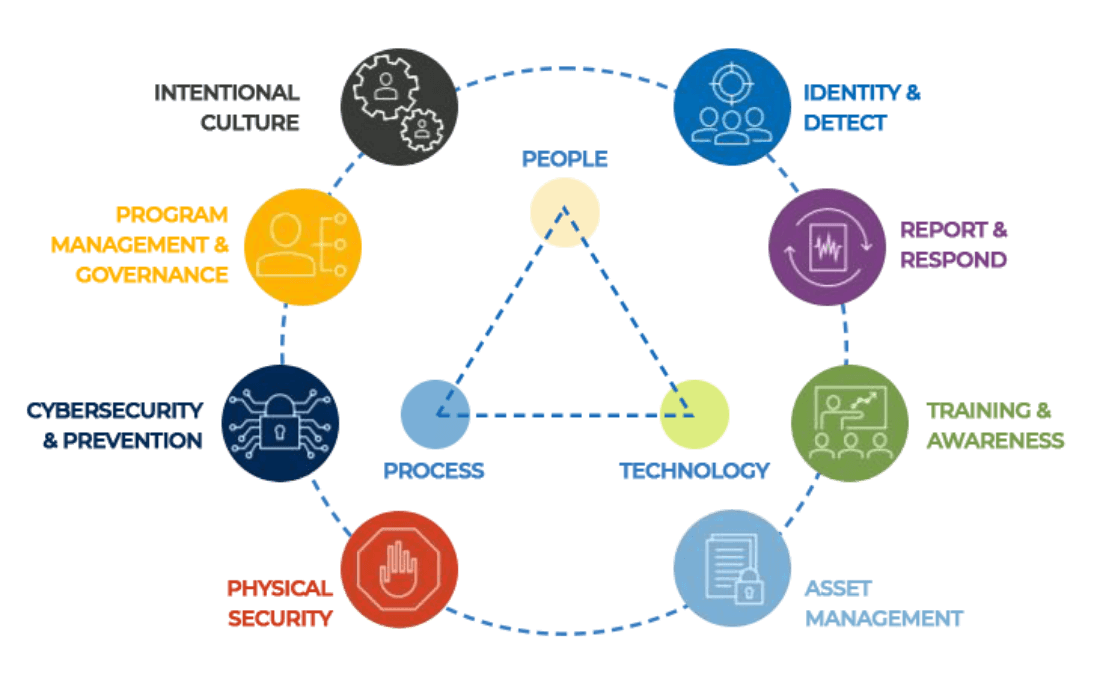
CYBER RISK MANAGEMENT
Tap Into Our Wellspring of Cybersecurity Risk Experience
We bring a wealth of experience and knowledge to the table to help you assess, analyze, and manage your cyber risk. Our experts possess deep industry knowledge, a solid understanding of the latest cyber security technologies, and a passion for helping organizations protect their data and systems. We have a proven track record of success, and are committed to providing you with the expertise and resources you need to successfully implement cyber risk management and transformation programs.

AVIH is a powerful and comprehensive automation and reporting suite designed to help organizations simplify their objectives and streamline operations. With AVIH, businesses can automate and streamline their tasks and operations with ease, allowing them to focus on their core objectives, such as growth and innovation.
AVIH offers a wide range of features and tools that can help businesses reduce their operational costs, save time and money, and improve efficiency. Additionally, AVIH provides detailed reports to help businesses gain insight into their operations and make informed decisions.
With AVIH, businesses can create automated workflows and processes, automate reporting and analysis, and gain visibility into their operations. With AVIH, businesses can also create personalized dashboards, set up alerts and notifications, and monitor performance. AVIH‘s features and tools are designed to help businesses maximize their resources and achieve their goals.
OUR CYBERSECURITY RISK
Security Development
Our cybersecurity development in AVIH is designed to ensure the safety and security of our data, services, and systems. We use advanced security measures, such as firewalls, intrusion detection systems, and encryption technologies, to protect our network, computers, and data from malicious attack.
We also have a team of experienced security professionals who are constantly monitoring our networks and systems for any potential threats or vulnerabilities. We also employ regular system updates and patching to keep our security measures up to date.
Additionally, we provide user training, awareness, and education to ensure that everyone in our organization understands the importance of cybersecurity and how to protect themselves and the organization from cyber threats.

Execute a Holistic Insider Risk Program
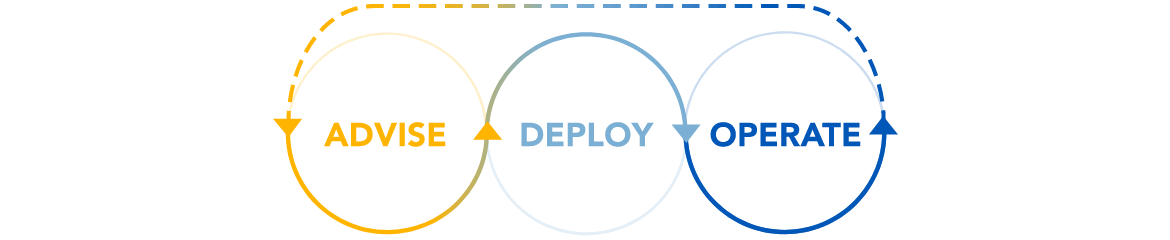
Advice and Strategize – Create a risk program that incorporates multiple techniques for monitoring insider behavior while minimizing false positives. Consider utilizing methods such as regular employee reviews, user activity monitoring, and security awareness training to reduce the risk of insider threats. Develop a plan of action to ensure the program is effectively implemented and maintained. Regularly review the program and make necessary adjustments to ensure its efficacy.
Deploy – Implement policies, procedures, and the appropriate technology infrastructure in order to create a benchmark for ordinary data access and vigilantly observe any policy infringements.
Operate and monitor – Monitor both on-premises and cloud security events in order to prioritize the security team’s efforts and to ensure personnel are adequately trained.
The AVIH Insider Risk Data Fabric Solution is a comprehensive solution designed to provide comprehensive visibility and context into the risk of insider threats within an organization. The solution collects and monitors data from multiple sources to provide a unified view of user activity and potential malicious behavior. This includes data such as user access logs, system access logs, and other relevant data points. The solution also provides real–time alerts and notifications of suspicious activity, allowing organizations to quickly respond to potential threats. Additionally, the solution provides detailed analytics and reporting capabilities, allowing organizations to identify trends and potential risks. Finally, the solution is designed to be integrated with existing security solutions, allowing organizations to gain a holistic view of risk.
"AVIH Team Has Been There, Done That"
Our elite teams will help you build an insider risk management solution tailored to your unique environment.
Adopting Zero Trust
Zero Trust is an approach to cybersecurity that is based on the assumption that no one is to be trusted, and that all network traffic must be authenticated and authorized. This approach is a departure from the traditional “castle and moat” approach to security, which assumes that all traffic within the “castle” is trusted and all traffic outside the “moat” is untrusted.
In a Zero Trust model, every user, device, and application must be authenticated and authorized, even if they are already within the “castle”. This approach ensures that only authorized traffic is allowed to flow within the network, and that all other traffic is blocked. This means that even if someone manages to access the network, they will not be able to move around freely within the system.
Zero Trust also employs microsegmentation, which divides the network into smaller, more secure segments. Each segment is protected by its own set of security controls, and no communication is allowed between the segments without explicit authorization. This makes it much harder for attackers to move laterally within the network and gain access to sensitive data.
Finally, Zero Trust also relies heavily on the use of analytics and machine learning to detect and respond to anomalies in network traffic. By utilizing these technologies, organizations can identify and block suspicious activity before it can cause any serious damage. In summary, Zero Trust is an approach to cybersecurity that assumes no one is to be trusted, and all network traffic must be authenticated and authorized. It employs authentication and authorization, microsegmentation, and analytics and machine learning to detect and respond to anomalies in network traffic.
Zero Trust is an information security model based on the principle that organizations should not automatically trust any user or device, regardless of their location or whether they are inside or outside of the network perimeter. This approach assumes that all users, devices, and networks are potentially compromised and must be verified before granting access to systems and data.
The Zero Trust model was introduced by Forrester in 2010 and has become increasingly popular as organizations look to improve their cybersecurity posture. The model is based on the idea that organizations should not rely on perimeter–based security measures such as firewalls and VPNs to protect their networks. Instead, it advocates for a multi–layered approach to security in which all users, devices, and networks are authenticated, authorized, and monitored for suspicious activities.
The core components of Zero Trust are identity and access management, network segmentation, micro–segmentation, analytics, and encryption. Identity and access management (IAM) is used to authenticate and authorize users, devices, and networks. Network segmentation is used to create logical boundaries between different parts of the network, while micro–segmentation is used to further isolate critical systems and data. Analytics are used to detect and respond to suspicious activity, while encryption is used to protect data in transit and at rest.
The goal of Zero Trust is to reduce the attack surface and make it harder for malicious actors to access an organization’s systems and data. It is not a one–size–fits–all solution and should be tailored to the specific needs of an organization. It also requires organizations to proactively monitor and detect suspicious activities in order to maintain secure networks and systems.
The Zero Trust Journey is a concept that has been gaining traction in the world of cybersecurity. It is based on the idea that no one should be trusted, and that all access must be verified and authenticated. This means that any access or communication request should be verified and authenticated before being allowed. In order to achieve this, organizations must create a secure perimeter of controls and continuously monitor the environment.
The Zero Trust Journey begins with a thorough assessment of the existing security infrastructure and the data flows within an organization. This assessment should include a review of the existing security policies, procedures, and technologies. The organization should then define their security goals and create a plan for achieving them.
Once the organization’s security goals have been defined, the next step is to implement the necessary security controls. This includes implementing network segmentation and access control lists, installing firewalls, and deploying endpoint security solutions. The organization should also implement identity and access management solutions such as multi-factor authentication and identity management systems.
The Zero Trust Journey also includes developing a comprehensive security policy. This policy should be regularly reviewed and updated to ensure that the organization is compliant with current security standards. The organization should also create a risk management program to identify, prioritize, and mitigate security risks.
The organization should also create a robust incident response plan. This plan should include procedures for identifying, responding to, and recovering from security incidents. It should also include the necessary personnel, resources, and processes for effectively responding to security incidents.
Finally, the Zero Trust Journey requires ongoing security training for all personnel. This training should cover topics such as secure coding practices, secure communication protocols, and security best practices. By training personnel in these areas, the organization can ensure that everyone is aware of the security risks and how to protect against them.
The Zero Trust Journey is a long and complex process. However, it is essential for any organization that wants to ensure that their data and systems are secure. By implementing the necessary security controls, creating a comprehensive security policy, and providing ongoing security training, organizations can ensure that they are taking the necessary steps to protect their data and systems.
A zero trust network is a cybersecurity strategy that is designed to protect an organization’s resources and data by limiting access to only those users who are authenticated and authorized. It is based on the assumption that all users, systems, and networks should be treated as untrusted, and access should only be granted based on trustworthiness. The primary goal of a zero trust network is to protect against malicious actors who may attempt to gain access to an organization’s sensitive information.
Zero trust networks are based on the principles of least privilege, which means that users and systems have access to only the resources they need to do their jobs. This means that access is granted on a “need-to-know” basis and only after authentication and authorization have been verified. Authentication is the process of verifying a user’s identity, while authorization is the process of determining which resources the user is allowed to access.
To ensure that users are who they say they are, authentication methods such as multi-factor authentication (MFA) and single sign-on (SSO) are used. MFA requires users to provide two or more pieces of evidence, such as a password, security token, or biometrics, in order to authenticate their identity. SSO simplifies user authentication by allowing users to access multiple applications and services with a single set of credentials.
Once users have authenticated, authorization policies are implemented to determine which resources they are allowed to access. Access is granted based on the user’s role within the organization and the level of access they need to perform their job. Policies can be set at the user level, the system level, or the network level. For example, a user may be granted access to certain files or applications, while the system may be configured to only allow certain types of traffic to pass through.
In addition to authentication and authorization, zero trust networks also employ other security measures such as continuous monitoring, data encryption, and secure access control. Continuous monitoring is used to detect any suspicious activity on the network, while data encryption ensures that any data transmitted over the network is secure. Secure access control ensures that only authorized users can access certain resources or data.
Zero trust networks are becoming increasingly popular as organizations look for better ways to protect their data and resources. By using a combination of authentication, authorization, and other security measures, organizations can ensure that only authorized users have access to the resources they need to do their job.
Zero trust architecture is a security model that is gaining in popularity as organizations strive to protect their data and networks from malicious actors. This security model emphasizes the need for a comprehensive security posture that limits access to any resource on the network to only those who have been verified as authorized users. This is achieved by limiting the access to resources to only those users who have been authenticated, and then further restricting the access of those authenticated users based on their roles and privileges. This means that no user can access a resource without first being authenticated, and even then, the access a user has is based on their role and privileges.
The concept of zero trust architecture is based on the idea that no users, applications, or services on the network can be trusted and must be verified before access is granted. To accomplish this, organizations must implement an authentication and authorization system that allows only those users who have been verified as authorized to access the network. This can be accomplished with a variety of methods, including two–factor authentication, biometrics, and digital certificates. Once users are authenticated, they can then be authorized to access certain resources, as well as be granted certain privileges or roles.
In addition to authentication and authorization, organizations must also implement other security measures to ensure the safety of their networks. These measures include segmenting the network into different zones, limiting access to specific resources and services, and monitoring user activity. With these measures in place, organizations can achieve a comprehensive security posture that prevents unauthorized access and limits the spread of malicious actors.
The implementation of a zero trust architecture is an important part of any security strategy. By ensuring that only authenticated and authorized users have access to the network and its resources, organizations can protect their data and networks from malicious actors. This security model also helps organization to better manage their security posture by limiting access to only those who have been verified as authorized, and by monitoring user activity. By taking these measures, organizations can ensure that their networks are safe and secure.
1. A Zero Trust security model requires that all users, regardless of their identity, location, or device, must be authenticated and authorized before accessing any resources.
2. All user access must be verified, monitored, and logged.
3. Access to sensitive data must be limited to authorized personnel only.
4. All network traffic must be encrypted to protect data in transit.
5. All data must be stored securely in accordance with industry-recognized security standards.
6. All devices must be regularly patched and kept up to date in order to protect against vulnerabilities.
7. All communications must be authenticated and authorized prior to transmitting data.
8. All users must use strong passwords and multi-factor authentication.
9. All users must be trained to identify and report suspicious activities.
10. All users must be aware of their responsibilities when it comes to secure data handling.
11. All security policies must be regularly reviewed and updated to ensure they remain effective.
12. All access control systems must be regularly tested and monitored for effectiveness.
13. All user access must be revoked when no longer needed.
14. All system administrators must be regularly trained in security best practices.
15. All system changes must be approved and tested before being implemented.

Understanding data
Where it is?
Why it’s important?
How it’s protected and who has access?

Snowballing change
Dealing with the scope and speed of the cloud, IoT devices and other DX activities.

Finding a collective pulse
Articulating risk and security to executives and boards in business terms.
Demystify the Revolving Door of Compliance in Cybersecurity Risk
The security and regulatory landscape changes so much that keeping up can become a real pain in the neck. And not keeping up – well, that can push your business onto the minefield of unidentified cyber risk.
Our comprehensive suite of compliance services covers:
Payment Card Industry Data Security Standard (PCI DSS) compliance includes four merchant levels, 12 requirements and lots of moving pieces – all of which are liable to change from year to year.*
Our complete solution set addresses increasingly complex healthcare-related privacy and security regulations while securing electronic protected health information (ePHI).
Our comprehensive framework takes an efficient and effective approach towards risk management, ensuring enterprises are within the guidelines of regulatory compliance.
We provide guidance to processes, technologies, security challenges and compliance standards to help you embrace digital transformation and secure your cloud environment.
We’ll help you develop an integrated, business-aligned control framework to manage and protect data according to external regulatory and other mandatory requirements.

Risk Automation
Our experts can automate and monitor risk mitigation in your environment by leveraging best-in-class GRC management platforms.
Risk Metrics & Reporting
We’ll develop KPIs and KRIs to effectively manage, monitor and improve capabilities within your security program.

