Cybersecurity Infrastructure
Secure your digital assets and safeguard your reputation by
implementing effective cyber risk management measures.
Cybersecurity Infrastructure
is a Business Strategy
Cybersecurity infrastructure is quickly becoming an essential part of any successful business strategy.
With the ever-growing threat of cyber attacks, it’s now more important than ever to ensure your business
is well-protected with the right security measures. By investing in a robust cybersecurity infrastructure, you
can protect your business from the risks associated with data breaches, malware, and other malicious activity.
Having a secure network is the foundation of any successful cybersecurity strategy. When establishing a secure network, it’s important to consider the components of the infrastructure, such as firewalls, antivirus software, and encryption tools. Each component plays a key role in protecting your business from cyber threats. It’s also important to regularly update your security systems to ensure they stay up-to-date with the latest threats.
In addition to a secure network, it’s also important to have a comprehensive security policy in place that outlines
the expectations and guidelines for employees. This policy should be reviewed and updated regularly to ensure that
it reflects any changes in the organization’s security needs. Training employees on cybersecurity best practices is also essential to ensure that everyone understands their role in protecting the business.

Consider your vast infrastructure: data, IoT, operational technology, cloud, endpoint, network security and physical security.
Protecting your vast infrastructure is essential for the success of your business. By implementing data security measures, such as encryption and authentication, you can ensure that your data is safe and secure. Additionally, deploying IoT and operational technology solutions can help monitor and control your environment, providing visibility and control over your assets. Leveraging cloud solutions can also help you maximize your data storage and access it from anywhere, while also providing additional security. Endpoint security solutions can add an extra layer of protection to your network, while network security solutions can detect and prevent malicious activity. Finally, physical security solutions can help protect your physical assets and personnel. By having a robust security strategy in place, you can make sure that your infrastructure is safe and secure.

Your infrastructure is under constant threat from a magnitude of evolving sources. Compliance is breathing down your neck and you need additional expertise.
Are you reaching for new security tools to plug holes? This reactive approach may solve short-term issues, but it ultimately results in an accumulation of disparate technologies with too few resources to manage them – increasing risk, complexity and inefficiency.
Every part of your infrastructure needs to be examined to ensure it’s operating efficiently, effectively and at scale.
The State of Your
Cybersecurity Infrastructure
Are you confident that your cybersecurity infrastructure is up-to-date and secure?
In today's digital world, cyber threats have become increasingly sophisticated, with new threats emerging every day. That's why it's essential for businesses to ensure that their cybersecurity infrastructure is strong and capable of protecting their data and assets.
From a security perspective, your cybersecurity infrastructure should include a combination
of hardware, software, and processes that help protect your data from unauthorized access and malicious attacks. This includes firewalls to block malicious traffic, encryption to protect data from being stolen, and multi-factor authentication to ensure only authorized users can access your systems.
You should also make sure that your cybersecurity infrastructure is regularly updated.
New malware variants, ransomware, and other threats can emerge at any time, so it's
important to stay on top of the latest security patches and updates. Additionally, consider conducting regular security tests and scans to uncover any vulnerabilities that could be exploited.
Finally, it's important to establish a cybersecurity policy and to train your staff on proper security practices. This should include rules around password management, data encryption, and other basic security measures.
By taking the time to assess the state of your cybersecurity infrastructure, you can ensure
that your data and assets remain safe and secure.
Consider your vast infrastructure
From state-of-the-art data centres to cloud hosting, our vast infrastructure gives you the reliable, secure and powerful platform you need to power your business. With full redundancy and cutting-edge security, you can trust us to keep your data safe and your systems running smoothly. Plus, our robust scalability options give you the flexibility to effortlessly adjust your resources as your needs grow and evolve. With our vast infrastructure, your business is ready for anything.

Each part of your cyber infrastructure has its own challenges. We help you thoroughly address each.
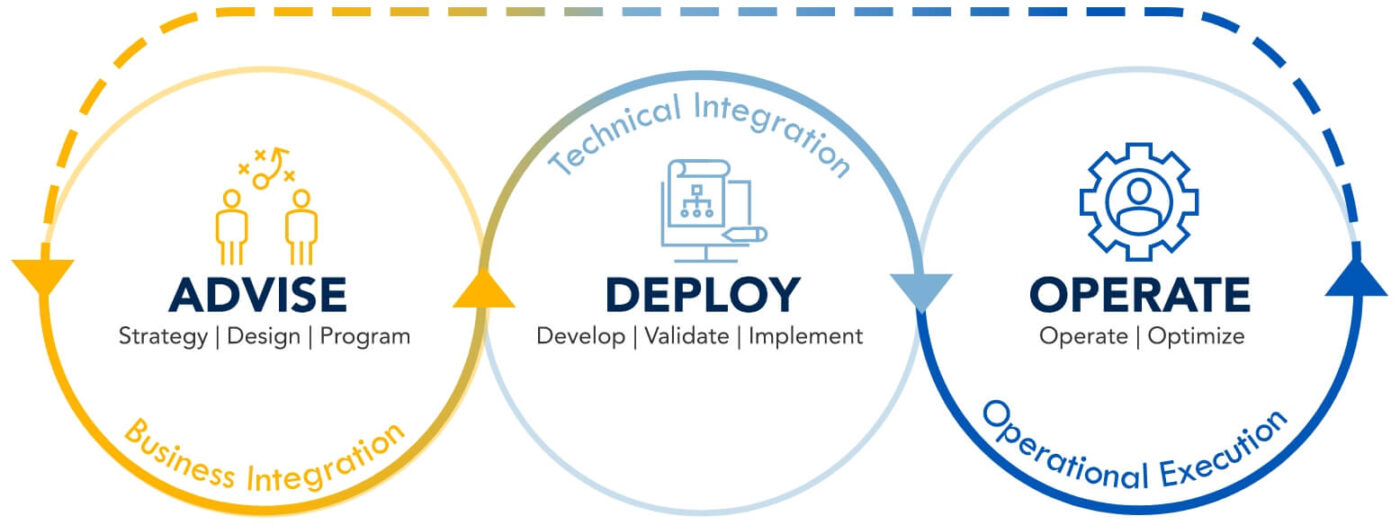
AVIH's Cybersecurity Infrastructure approach includes:
Get security technology off the shelf and deployed efficiently –
Integrate siloed security technologies and processes to help maximize
the investments you’ve already made.
Solve your talent gap – Bring in the experts to solve your pressing infrastructure
challenges now and plan for the future.
Then we help corral your data issues. Our data fabric solution gives a programmatic,
technology-agnostic approach to increase the value of your data.
Our integrated technology bundle, paired with service enablement,
helps you deploy, configure and run a resilient data management solution.
Most companies only analyze
12% of the data they have.
You got it, that means
88% of data goes unanalyzed.
*Forrester: Insights-Driven Businesses Set The Pace For Global Growth
Each part of your cyber infrastructure
has it's own challenges.
AVIH’s Cybersecurity infrastructure approach includes:
Keeping your network secure and up-to-date is essential. To protect your business from cyber threats, each part of your cyber infrastructure—from the hardware and software to the data and networks connecting them—needs to be secured and monitored. From firewalls to anti-virus software, you must have the right tools in place to ensure your business is protected from cyberattacks. Additionally, your business should regularly update it's software, systems, and networks to maintain the highest levels of security. By staying ahead of cyber threats and ensuring that each part of your cyber infrastructure is secure, you can keep your business safe and successful.
Overcoming Cybersecurity Infrastructure Challenges
With a secure, sustainable data framework and governance model to drive data value you will conquer:

Your Data Explosion
Understand, manage and create actionable insights from terabytes of data, wherever it lives.

Lack of Data Digital Security Management
Get adaptable security guardrails (not gates)
to securely connect tech and people to
business and policy.
The Data Management Talent Shortage
Reduce reliance on scarce data, IT and security skills by augmenting.
With our comprehensive data management solution, you can reduce costs through tech consolidation, better identify and manage risks,
and reduce your reliance on scarce data, IT and security skills. By taking advantage of our solution, you can gain a better understanding
of what is really happening in your business and ensure that your data is secure and protected.
Enjoy the peace of mind that comes with knowing that your data is managed in a safe and secure environment.
Build a More Effective Cybersecurity Infrastructure