IDENTITY ACCESS MANAGEMENT
In AVIH, the benefits of cloud computing and flexible working patterns make it possible for teams to be productive no matter where they happen to be physically located. However, a global shortage of expertise presents some unique challenges. Projects involve a multitude of actors from self-employed individuals to consultancy firms, increasing inconsistencies, financial risk and therefore, project failure. At AVIH, we’re aware of these challenges and understand how to overcome them.
We are proud to be one of the leading experts in Identity Access and Management. Our team collaborates daily to offer you our renowned high-quality services.
Our team of experts has developed an innovative methodology over the course of more than a decade, allowing us to maintain a 98% customer retention rate.
Our top priority is customer satisfaction. To that end, we take a technology-agnostic approach and recommend the right solutions for your needs. We have developed our centers of expertise with market leaders as well as emerging start-ups.
The firm’s global federation provides a multilingual and multicultural approach to everything we do.
OUR SERVICES
We offer three specialized service areas: Advisory, Implementation and Managed Services. These can help businesses like yours at different stages of their journey, from full implementation to ongoing operational support as business practices evolve.
ADVISORY SERVICES
If you need help getting your business into a new way of working, or are dealing with an existing situation and aren’t sure how to handle it, we can assist you.
We often assist businesses that are confused about their technological needs or have outdated technologies in need of an extensive review.
We assign our most experienced consultants to your project. Their experience as Project Managers, Business Analysts, and Technical Architects ensures they’re perfectly positioned to gain a complete understanding of your challenges and help you to overcome them.
Our customer-centric strategy will provide you with a positive experience at every stage of your journey.
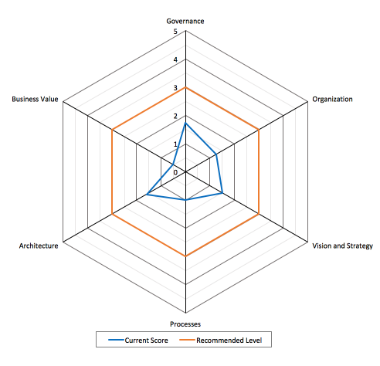
Maturity Assessment
During an IAM Maturity Assessment, we study six elements and execute a Gap Analysis against the recommended level:
- Governance: Does the IAM initiative have executive sponsorship? Any formal structure in place?
- Organization: Is there any organizational structure to manage IAM ? Are roles and responsibilities clearly defined? Are the individuals managing these areas being supported?
- Vision and Strategy: Is there a clearly defined roadmap in place? Is there any formal planning to achieve the strategy?
- Processes: What is the existing operating model and what processes are in place across the organization relevant to IAM?
- Architecture: How are the IAM Architecture and Infrastructure mapped to the overall Enterprise Architecture and business processes in general? This includes the technologies in place with regards to IAM.
- Business Value: How do IAM initiatives contribute to the business: security, automation, compliance….?
In a nutshell, your maturity assessment will answer these questions:
- Where are we?
- Where do we want to be?
- How do we get there?
- We listen to your answers, and we deliver the solution that’s right for you.
Technology Vendor Analysis
AVIH, has partnered with over 90% of identity and access management vendors on the market.
Our hands-on approach ensures that we are always up to date on the latest technologies, so that we can recommend only those systems and platforms that will work best for you.
We test new products and services in our lab, so that we can offer demonstrations as well as practical advice. Our experts stay on top of the latest trends by researching niche vendors and smaller firms, as well as well-known companies.
Vendor Selection Process
Identifying the most appropriate vendors for Identity and Access Management can be challenging. With so many to choose from, it can be difficult to differentiate and select the solution that will add value. That’s why the AVIH team saves you time by finding the best solution for your specific requirements.
We shortlist the top 2-3 IAM vendors that meet your needs. We do this by prioritizing your requirements and using a scoring system to filter out the perfect vendors.
Our experience tells us that all the good vendors can satisfy the basics of IAM, so we avoid spending time in that area and instead focus on the more challenging questions that will put you on the right course.
Our team works hand in hand with your procurement team to ensure the best license deal is obtained.
IMPLEMENTATION SERVICES
Our implementation services include business consultancy as well as technical implementation because both elements are crucial to a successful outcome. We believe in one coordinated team of experts following our customers over time and across all IAM disciplines. This reduces the chances of any key components slipping through the cracks, or any overspend on non-essential areas.
Working with us allows you to benefit from the experience of a team made up of Program and Project Managers, Business Analysts, and Technical experts. We build project teams that include your staff members and train them along the way to facilitate knowledge transfer and operationalise your framework.
Our Technology Practice
Our expertise is global and falls into three distinct services and technologies:
- Identity Access Governance (IAG)
- Privileged Access Management (PAM)
- Access Control (Authentication and Authorisation Management) which includes Customer IAM (CIAM) and Open Banking associated projects.
We work with leading solution providers as well as niche vendors in the EMEA market.
Let’s get to the root of your challenge
As trusted advisors and integrators, we establish and develop relationships with our customers to provide strategic planning and custom solutions. Our customers rely on us for the expertise required to meet their business challenges.
Identity and Access Management brings a variety of lifecycles in constant evolution. Understanding this challenge is understanding the need for a modular and agile approach.
The longer your delivery lifecycle for Identity and Access Management is, the more chance you have of the project being impacted or failing, due to these small changes. We make sure this doesn’t happen.
We have developed our methodology and applied it to IAM projects for over a decade.
Our Methodology
We have developed and fine-tuned our methods over time, and the experience held within our federation has expanded greatly.
Our methodology is continuously evolving, and we rely on these four fundamental principles:
- Short delivery cycles. We break down complex use cases into smaller projects that are completed within eight weeks.
- MI reporting. IAM programs include many stakeholders and use a common language to communicate: we help you establish a common language along the project’s life cycle with Meaningful Indicators (KPIs, risks indicators).
- One team. We consider your team and ours to be equal partners; all of us share our expertise from the beginning, for maximum efficiency.
- Quality before quantity. Our delivery teams consist of Senior Specialists and Subject Matter Experts so we can deliver the highest quality services.
The demand for IAM expertise is higher than the available supply, leading to high turnover for many organizations.
We provide a range of Managed Services from simple technical support to the complete outsourcing of your Identity and Access Management operations.
How our managed services work
We will act as your partner. Our managed services are built on four principles.
- Eliminate dysfunctional turnover. With our help, you won’t need to maintain an in-house niche skill set for Identity and Access Management.
- Reduce costs. Decrease staffing overheads with a specialized team of dedicated professionals.
- Reduce operational overheads through optimised monitoring, reporting, and escalation processes which ensure your Identity and Access Management infrastructure runs at maximum efficiency 24/7.
- Improve the speed of resolution, relying on a dedicated and experienced team of experts.
Technical support, including issue diagnosis and resolution
Our team investigates problems and diagnoses issues. If you need information, we can provide technical guidance.
Pro-active monitoring of your Identity and Access Management systems
We provide regular health checks and monitoring services to ensure your systems are running as expected. We examine log files in detail and correct any issues, a proactive approach that usually leads us to identifying problems before they impact users.
On-site technical assistance for major incidents
When you experience an access management incident, we’re here to help. We can recover data and repair systems, all while taking care of you and your clients.
System administration to help reduce the in-house burden
We take over the burden of hiring an in-house system administration team, so you can focus on your core business. We resolve any point of failure and maintain your system daily.
Monthly MI reporting with agreed KPIs
We help you to keep your team on task, by reporting on your progress against KPIs and KRIs. We can also integrate with your Operational Risk framework to provide a holistic approach to managing risk.
GENERAL FAQs IAM
How do we work?
AVIH, your trusted partner in Identity and Access Management, is dedicated to meeting your needs. We will work with you from day one to make sure our solution matches the requirements of your business.
Our risk management experts will help you identify and assess the risks involved in your business plan. We’ll also ensure that all parties are aware of your proposed solution and able to support it.
Our team of Strategy and Business Analysts, Technical Architects, and Project Managers will ensure that your solution is implemented correctly. We can also assist you with support long after the implementation phase.
Who are our experts?
Our team includes Technical Architects and Developers, Business Analysts, and Project Managers who have spent many years mastering the intricacies and ever-evolving landscapes of Identity and Access Management.
The importance of Identity Access Management (IAM) is on the rise with ever-changing complex compute environments and increasing security threats. IAM incorporates elements of biometrics, machine learning, artificial intelligence (AI), risk-based authentication, and identity-as-a-service (IDaaS). A data breach report from Verizon indicates that 97% of breaches are preventable—making a good case for IAM.
Why Identity and Access Management?
- in help desk calls for IT support on password resets
- Allows administrators to automate IAM and save time costs enhance service delivery
- IAM helps IT teams to define access policies for whom and which data to be given access
- Better control of user access reduces internal and external breaches
